LeHack, Client Side vulns
• public
Table of contents
Last week, it was finally LeHack event, and it was really cool. I was able to use my automation to shine during the LHE.
Before that, I also finished building the base of my automation to have something usable for this event.
And as I told you, I'm now looking more into client-side vulns and I'm learning how to dig deep into this type of vulns.
Automation
To summarize what I've done last week about automation, I finished having my n8n setup to scan a target and get any data from the scan.
I also built a caido workflow to help me find XSS and secrets.
At the end of the week, I finally decided to buy a short domain to have better options if I find an injection point with a limited number of characters. I found a 4 characters domain, using Unicode characters with this https://github.com/ssl/shortboost
On this domain, I just put an ezxss for the blind xss and also an interact sh server to monitor any ssrf payload. I used this great article to setup everything :

So the plan with all of that was now to try it on a real target, and here the LHE at LeHack comes!
LeHack
That was really great. I was able to see again a lot of great hunters and friends. I attended some conferences, and one from @shutdown about how to find a career in cybersecurity. That was very interesting and he asked me some questions about my life as a full-time hunter.
Another great part was that I was invited to a private evening with other hunters, and it was really nice to meet them again and to discuss with some program managers of programs I'm used to hunting on. After that, I wanted to go back and hunt them.
We also got some nice goodies. The usual t-shirts, and also nice stuff from YesWeHack.
But for me, the aim of this event was the LHE and my ability to try my new automation on a real target. So on the morning of the LHE, I was with some friends waiting for the scope and the scope was L'Oréal.
At the beginning, I just started to go on each website to see which one I would focus on and at a moment, I saw in my Caido some Findings detected from my custom plugin. I was like, no it's impossible to already get something. And yes, after 5 minutes I got a hit for an XSS. I immediately reported it to be the first one, and then I searched more to increase the impact and get an ATO. With the help of some friends, I got a nice poc to steal the password of the user, and the XSS was rated as High.
So, my automation setup was working pretty well. As this target wasn't really what I like to search for ( mainly salesforce commerce, not a lot of custom stuff ), I decided to stop here looking at L'oreal and I hunted on my other target. I just wanted to be sure my plugins worked, and it was good, I made some money during the LHE. Then during the night, I continued hunting on other targets, and I found pretty juicy stuff, so that was rewardful at the end.
But in my opinion, this kind of event is not very the occasion to make a lot of money but more to discuss and see your friends, hunt together and so on. Because during this king of LHE, it's more a race than really searching for big bugs. As we don't know what to target before, everyone will look at the same ones and find the same bugs, so you will have to be the first. So if it was your first LHE, don't worry if you didn't find anything!
Client Side vulns
I'm currently learning a lot about client-side vulns and stuff. There are so many little gadgets, it's very interesting as it can really help me leverage a lot of vulnerability.
To learn that, I got a nice book from Garet Heyes Javascript For Hackers. I'm also looking at the MDN doc to learn everything, and I'm playing with domloggerpp to understand how this stuff works.
In the next weeks, I will try to write more technical articles about tips and gadgets you can use on the client-side to help you and to have somewhere to get this information other than in my head.
Ideas / Notes / Resources
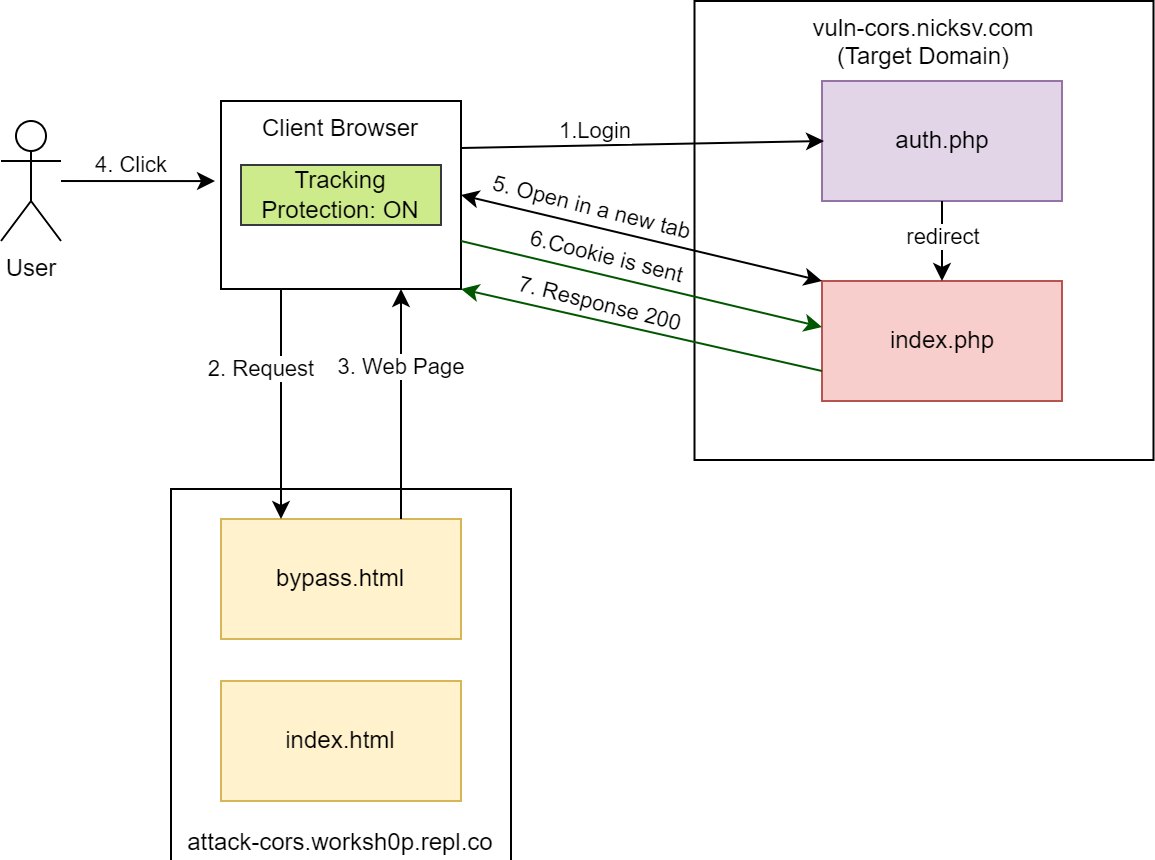
- Some tricks to understand how CORS works
- A great article about imposter syndrome